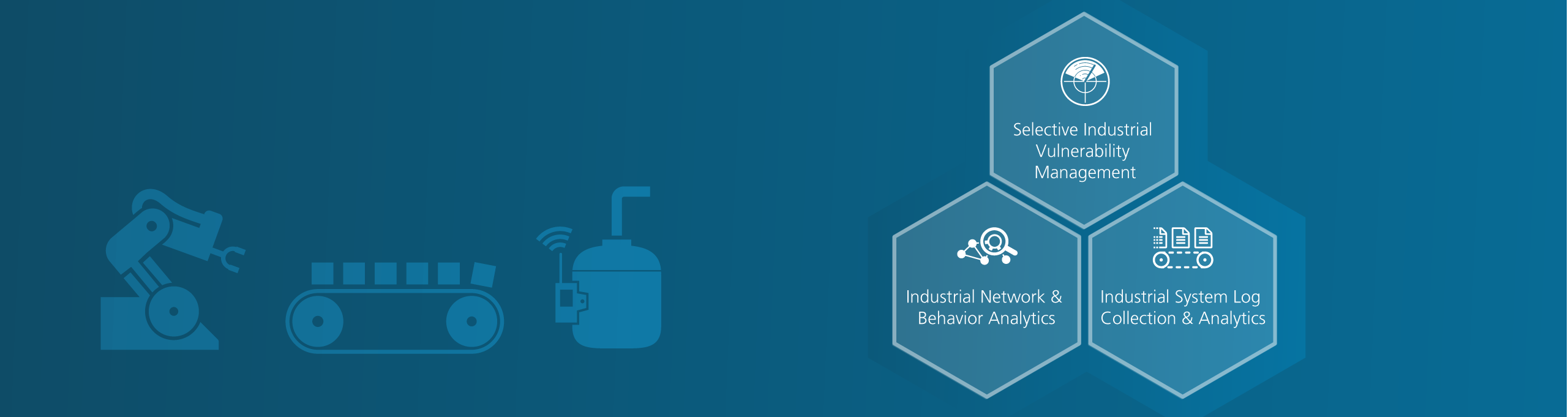
Collection, analysis and the correlation of logs from different sources in the OT/ICS environment in order to alert in case of security problems or potential risks.
Identifying protocols and applications in the network traffic, analyzing the extracted data and visualizing anomalies provide clarity about the current situation.
The Deep Packet Inspection solution classifies and decodes data streams down to the contents thereof. Authorized protocols are thus also checked for hidden attacks. Security problems originating from infected machines, incorrect configuration or potential cyber attacks are detected.
Selective Vulnerability Management and Assessment (VAS) is performed in selected areas and environments. The assessment does not cause any disruption to the availability or integrity of data.