Continuous IT security monitoring provides an overview of the security-relevant information of the organization’s entire IT landscape at the push of a button, as an integrated solution requires an integrative offer that comprehensively supports the company.
Only with a tried and tested process and proven technology is it possible to shorten reaction times and optimize existing processes. The Radar Cyber Security Cockpit provides an overview of a company’s IT infrastructure, showing everything that happens, including large and small security incidents. It is easy and simple to assess and monitor the risk of vulnerabilities. Processes become complex, elaborate and multi-layered when behavior-based methods such as Log Data Analytics (LDA) or Network Behavior Analytics (NBA) are added.

The result is that all relevant incidents are reported. Any incidents that have been discovered are discussed in regular meetings with the customer, and attention is always drawn to the risks that have been indicated or that are to be clarified. These must be examined and resolved by the IT department and/or the IT officer.
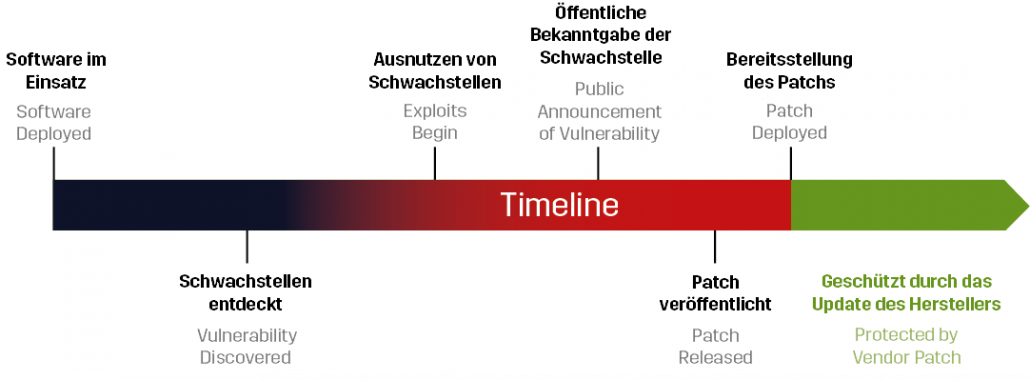
Vulnerability timeline
The unfavorable time
Vulnerabilities can be exploited until a patch has been successfully installed, which means early detection should therefore be a top priority for companies.
The following time line for vulnerabilities and their exploitation is derived from software:
- A piece of software is developed and published.
- The vulnerability is discovered and known by researchers or attackers. This presents a golden opportunity for attacks. It will however take some time before the vulnerability can be successfully exploited.
- The vulnerability will be made public. Ideally, the manufacturer has already identified it themselves and is working on fixing the vulnerability. However, there is still ample opportunity for attacks.
- The manufacturer is working on the patch to fix it and releases the update to fix the vulnerability.
- This vulnerability can no longer be exploited only once the company has successfully installed the patch. This closes the window of opportunity for hackers to attack.
What needs to be done in a worst-case scenario?
Fire on the roof? What do you do when your house is on fire?
You put out the fire. Or you call the fire department.
What do you do if your IT infrastructure is infected or attacked by malware?
Do you call the IT department, the CEO or your CISO? Or do you even know if and how you are protected, which and how many devices are connected and where your vulnerabilities are?
But a single fire extinguisher is not enough. Monitoring all networks requires know-how – and above all IT experts. Only when IT infrastructures are continuously monitored and risks analyzed can a reliable overview be created. This information, along with any security alerts, is clearly displayed in the Risk & Security Cockpit.
Imminent danger
A lack of corporate security policies and cyber security awareness are the perfect conditions for successful cyber attacks.
If old or even infected servers are integrated into the company’s network and the antivirus software is deactivated or obsolete, disaster won’t be very far behind.
The situation becomes particularly serious for companies when BotNets, Emotet, Bank Trojans and other malware endanger the company’s network and even threaten to paralyze it.
If the necessary attention is not paid to these risks, or they are even ignored, the threat quickly escalates. After all, the entire company might then be brought to its knees.
In case of emergency: Step up efforts!
That is why responsibilities must be jointly defined. In the event of an emergency, companies set up an internal task force to resolve these incidents as quickly as possible and get to the root of the problem. Radar Cyber Security naturally provides advice and support to customers in these situations from the outset. Radar Cyber Security also has its own internal task force to support customers in such acute cases.
If the company’s network is affected by numerous malware infestations with varying degrees of severity, on-site meetings will be scheduled. In such extreme emergencies, it is necessary for the Radar Cyber Security Forensics Team to be deployed so as to more accurately examine and monitor endangered IT and OT infrastructures.
Code Red!?
In a worst-case scenario, the Incident Response Team makes daily calls to customers to determine the course of action, reassessing and evaluating risks and threats on a daily basis. Radar Cyber Security’s experts help customers resolve incidents and threats. Weekly service intervals are also shortened to daily service intervals.